What is Release Management and How Does it Work in Regulated Industries?
There was a time when engineering teams literally taped release artefacts to secure IT room walls. CDs sat in safes, deployment schedules were printed under glass, and auditors signed physical paper sheets to verify compliance.
But today, your releases need to be fast. Customer expectations don't wait for quarterly deployment windows—and engineering leaders continue to face pressure to modernise and automate.
In data-sensitive and regulated industries, every release carries real risk.
However, modern release management bridges this gap by proving you can automate without losing oversight and move faster while staying safer. The old wall charts have now been turned into digital dashboards, and many engineering teams ship multiple times each day. But they can only do it with specific controls that make it possible.
This guide shows you how to build release management processes that help you ship faster, with confidence every single time.
Why modern release management matters in regulated industries
When you work in a regulated industry, every release feels like a tug of war. On one side, product teams push for faster delivery and experimentation. On the other hand, compliance officers and risk managers insist on airtight controls.
Too often, enterprises treat this as impossible: either ship quickly and risk exposure, or move cautiously and frustrate the business.
Inside your own walls, you’ve probably felt the tension too. Your leadership demands speed, compliance insists on control, and engineering teams are stuck in the middle. Without a modern release management approach, every side loses.
And the cost of clinging to legacy release cycles is steep:
- Downtime and outages when big-bang releases go wrong.
- Audit failures due to incomplete records and manual processes.
- Lost market share as competitors roll out updates in days instead of months.
- Burnout and morale issues as engineers brace for high-stakes “release weekends.”
Case in point: TSB, a British bank, was fined £48.5 million for a failed IT migration in 2018. The company executed a Big Bang deployment to migrate 1.3 billion customer records—but things went wrong, resulting in lost access to records and data breaches. It was a clear-cut release management failure.
When you move towards modern release management practices, there are ways to reduce risk. For example:
- Automation allows for consistency, so fewer releases fail due to human error.
- Audit logs provide traceability for every approval, rollback, and change.
- Feature flags decouple deployment from release, letting you roll out gradually without exposing all users at once.
- Continuous feedback loops mean you’re learning and adjusting in real time instead of waiting for quarterly reviews.
You’ll experience faster delivery cycles, fewer compliance headaches, and more resilient systems. Your release management process becomes less about firefighting and more about creating a repeatable, trusted process.
5 core phases of an enterprise-grade release management lifecycle
Your release management lifecycle needs to balance speed with the rigorous controls that regulated industries demand.
Think of it like air traffic control—you need systematic processes that handle multiple moving parts while maintaining safety at every step.
Here are the different phases of release management:
- Planning & requirements gathering: This isn't just about listing features. In regulated industries, planning means defining risk categories, mapping compliance requirements, and documenting approval gates upfront. When code hits your pipeline, everyone should know who signs off and what evidence auditors will need.
- Building and automated testing: Automated unit, integration, and security tests enforce quality without slowing teams down. In practice, this phase reduces the cognitive load on engineers. You can trust your pipeline to catch the basics so human reviewers can focus on higher-value risks.
- Pre-release staging and controlled rollout: Here's where deployment separates from release. You can deploy code into production, but hide the code behind feature flags or staged environments. Canary releases let you test with a subset of users, while dark launches expose functionality without making it visible. Both strategies lower the blast radius when things go wrong.
- Deployment and monitoring: Shipping to production isn’t the finish line—it’s the starting point of oversight. Real-time dashboards track latency, error rates, and compliance-related metrics like data access. The ability to roll back instantly is as critical as shipping forward.
- Feedback loops and iteration: Enterprises often treat releases as one-way doors. Modern release management makes them loops. Telemetry data feeds into planning, compliance logs are reviewed for gaps, and business outcomes are compared against release goals. Each cycle should sharpen the next.
Best practices for better and safer software releases
Walk into any bank, healthcare organisation, or any other regulated organisation today, and you'll find teams caught between two impossible demands. Move faster to stay competitive, but don't break anything that could trigger compliance issues.
Here are a few ways you can lower the level of risk if you’re moving towards modern release management:
1. Use CI/CD and automation to improve release quality
Your CI/CD pipeline helps you enforce quality at scale. It runs security scans, code quality checks, and regression tests that would take manual teams weeks to complete. Every code change or decision your team makes gets logged automatically with timestamps, user IDs, and change descriptions.
As a result, you'll catch issues early instead of surfacing during a live release. Plus, your auditors get the paper trail they need. Your teams stop spending hours on manual documentation.
For example, organisations like Komerční Banka integrated Flagsmith into modern CI/CD pipelines for frequent, safe production deployments. They used automated approval flows and granular rollout mechanisms to ensure that every release is safe and compliant.
2. Take advantage of feature flags to decouple release from deployment
This separation changes everything about how you manage risk.
You can deploy code to production infrastructure without exposing it to end users. So, you can test with real data and traffic patterns while controlling who sees new features. Or roll back problematic functionality instantly without touching your deployment.
Some examples of such strategies include:
- Canary releases: Start with 1% of traffic, gradually increase exposure as confidence builds
- Ring-based deployment: Roll out to internal users first, then beta customers, then everyone
- Progressive delivery: Launch specific features to a small subset of users and expand based on more granular aspects like geography, user segment, etc.
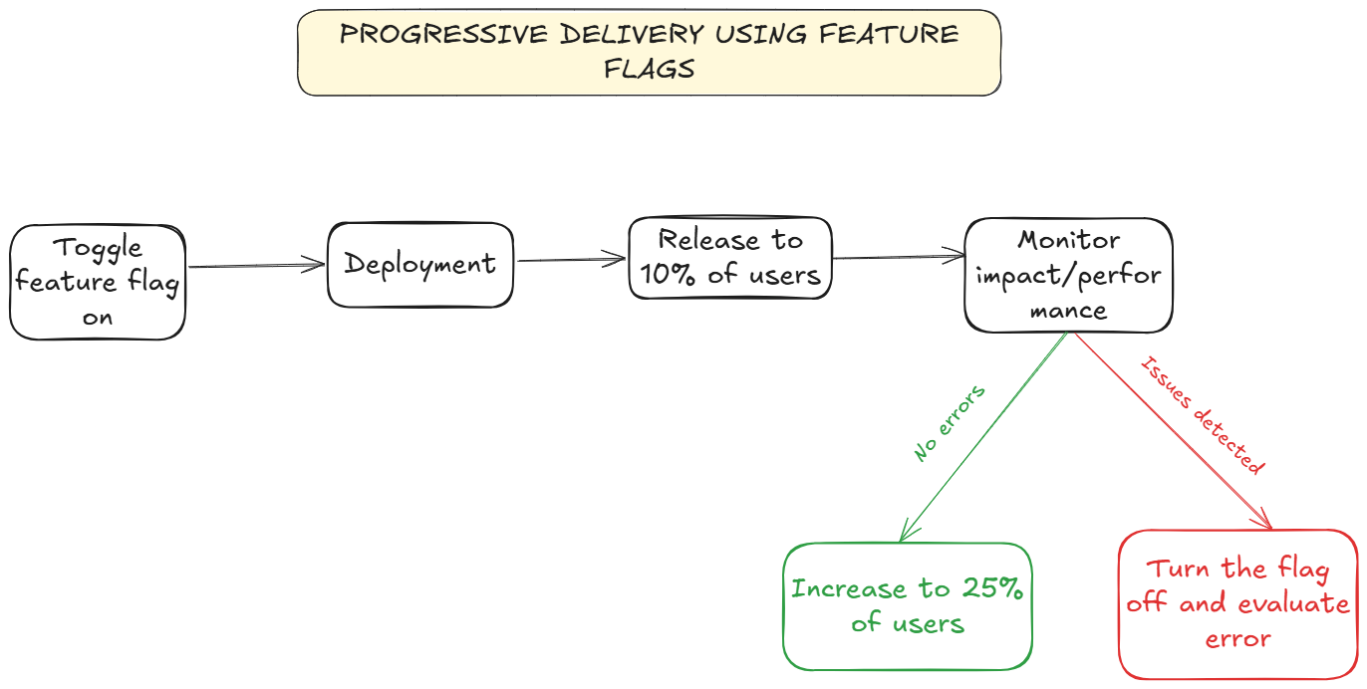
Most teams discover that feature flags solve problems they didn't even know they had.
For example, developers at OakNorth Bank roll out new features (e.g., new interfaces or account types) behind feature flags. They launch internally, then for limited customer segments, and gradually to all users. This minimises risk, and if issues arise (performance, compliance, user experience), the feature can be instantly toggled off, repaired, and retested before a full-scale launch.
3. Implement guardrails for compliance, governance, and collaboration
Documentation and sign-off workflows should feel natural. You can move quickly without straying into non-compliant territory when you have guardrails. Here are a few governance controls you can consider using:
- Role-based access: Different permission levels for developers, approvers, and emergency responders
- Automated approval workflows: Route changes to the right reviewers based on risk level and scope
- Audit trail generation: Complete history of who changed what, when, and why
🏴 Pro tip: Flagsmith offers governance controls like change requests (4-eyes approval, audit logs, and RBAC to help engineering teams maintain control.
4. Conduct regular user testing to make sure everything works well
It's always best to test in production and live environments with real users to catch issues you might miss in staging environments. You'll come across edge cases and performance issues that are hard to find with synthetic data.
Consider using feature flags for beta or shadow testing (A/B testing) to limit initial exposure to users who understand they're seeing experimental functionality.
Companies like Delinea have switched to this approach to validate and iterate on new product features before deploying to production. They gather real-world feedback before rolling features out through gradual releases. As a result, they don't have to worry about coordinated releases.
5. Use a dynamic software release calendar
Software delivery has two extremes: rigid quarterly release calendars or ad-hoc releases. Neither approach works anymore because there's an element of chaos in both. While rigid calendars add unnecessary pressure, ad-hoc releases leave too much room for confusion.
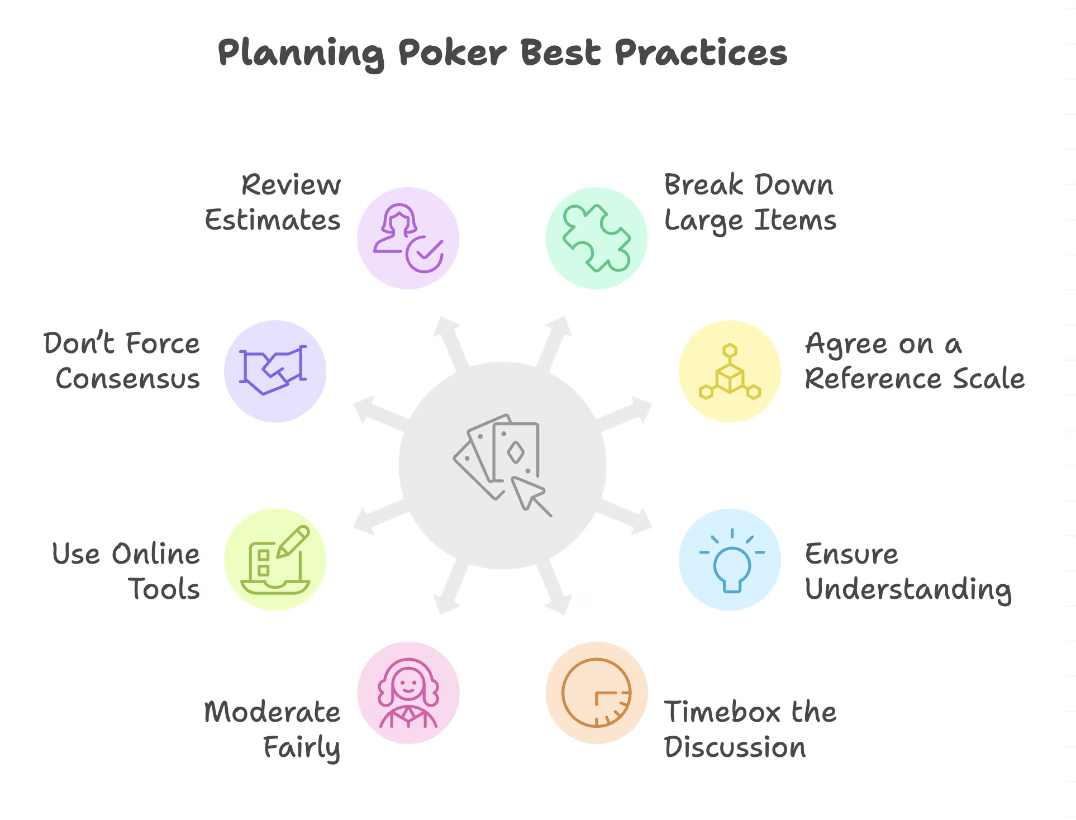
That’s why you should consider using the planning poker technique to make accurate estimations. It accounts for:
- Testing requirements
- Compliance reviews
- Coordination overhead
- Hidden dependencies
Pair that with a dynamic release calendar with planned dates, but a one or two-week buffer in case you need more time.
🏴 Pro tip: A dynamic release calendar works best with transparent communication. Publish planned rollouts in a shared tool like Jira or Slack, so every stakeholder knows what's coming next.
Pitfalls you can expect (and avoid) with release management
Even teams that understand modern release management principles still fall into predictable traps. Here's what actually goes wrong in the real world, and how to avoid these costly mistakes:
Over-automation without oversight
Automation feels like the answer to everything until it isn't.
Many engineering teams get so excited about removing manual bottlenecks that they automate away essential human judgment points. This typically happens when teams automate their entire deployment pipeline without maintaining manual override capabilities.
You can avoid it by keeping humans in the loop for high-risk decisions. For example, don’t automate anything related to security exceptions or emergency deployments.
Lack of governance controls
This one hits teams that move fast without building proper guardrails. They implement continuous deployment but forget that "continuous" doesn't mean "uncontrolled." For example, your developer might accidentally push code that exposes sensitive data or automate deployments that aren't exactly compliant.
Don't optimise for speed. Instead, build governance into your pipeline. You can use platforms that offer role-based access controls so that only the right people can push code into production after reviewing it.
Not communicating enough internally
Release management breaks down when different teams operate with different information. Engineering thinks the deployment is ready, compliance thinks more testing is needed, and business stakeholders have no idea what's happening.
Each team has their own definition of "ready to deploy."
To avoid this, ensure everyone has visibility into what's happening. Align on what "readiness to deploy" means and use a shared calendar or dashboard so that everyone can access the same information.
Not accounting for technical debt
It's easy to recognise technical debt in code but miss it in processes. And as you keep deploying more code, it only increases with time—eventually becoming a headache to clean up later.
So, treat your release process like code and refactor it regularly.
You can schedule quarterly reviews of your deployment procedures and make technical debt one of the items on the agenda. Or even make sure your automation platform runs static code analysis, dependency checks, and security scans to flag these early on.
But most importantly, make the debt visible. Document explicit tickets or stories with clear descriptions and business impact so that you know when to take them down. Add a lightweight "lessons learned" review after every major release. It surfaces hidden debt so that you can clean it up later.
Enterprise release management checklist
Quick assessment for engineers and architects to evaluate release management maturity.
Release planning:
✓ Risk assessment included in every release plan
✓ Cross-functional teams involved in release planning
✓ Clear approval workflows defined by change risk level
✓ Rollback procedures documented and tested
✓ Stakeholder notification process established
CI/CD pipeline:
✓ Automated builds trigger on every commit
✓ Security scanning blocks vulnerable deployments
✓ Comprehensive test coverage (unit, integration, regression)
✓ Automated deployment to staging environments
✓ Manual approval gates for production deployments
Feature management:
✓ Feature flags enable deployment without release
✓ Progressive rollout capability (1% → 100% traffic)
✓ Emergency kill switches for instant feature disable
✓ Flag lifecycle management prevents technical debt
✓ Production testing framework with controlled exposure
Monitoring & response:
✓ Real-time deployment status visibility
✓ Business metrics tracked alongside technical metrics
✓ Incident response procedures with clear escalation
✓ Post-deployment health checks automated
✓ Comprehensive audit trails for all changes
Team process:
✓ Regular retrospectives improve release process
✓ New team member onboarding for deployment procedures
✓ Release calendar coordinates with business priorities
✓ Cross-team dependencies documented and tracked
✓ Quarterly process reviews drive continuous improvement
Building confidence with modern release management
The days of taping release artefacts to secure IT room walls feel like ancient history now. But the underlying challenge hasn't changed.
You still need to balance speed with safety, innovation with compliance, and automation with oversight. Modern release management shows you don’t have to. Here’s how:
- CI/CD pipelines reduce errors and remove manual burden
- Feature flags give you control over exposure
- Compliance guardrails ensure every change is auditable
Together, these practices dissolve the false trade-off between agility and oversight.
Feature flags become your safety net, letting you deploy code confidently while controlling exactly who sees what functionality when. If you adopt them fully—especially progressive delivery with feature flags—you can experience faster delivery, safer systems, and more trust across teams.
The choice is yours. It's time to modernise your release process; every deployment becomes a confident step forward.
Frequently asked questions
1. How can CI/CD principles be applied in regulated industries?
CI/CD strengthens compliance by providing better audit trails than manual processes. The key is building governance into your automation rather than around it. To stay compliant, use automated approval workflows, comprehensive logging, and role-based access controls.
2. What's the role of a release manager, and who handles it?
In mature organisations, a dedicated release manager orchestrates across these functions, but the work is distributed. However, the organisation rotates this coordination responsibility among senior engineers in small teams.
3. What role do feature flags play in modern release strategies?
Feature flags are the foundation of modern release management because they decouple deployment from release. You can deploy code to production infrastructure without exposing it to users, test with real data while controlling exposure, and roll back problematic features instantly without redeployment.
4. How can release processes be both agile and compliant?
Build compliance into your agile processes rather than adding it as a separate step. Use automated compliance scanning in your CI/CD pipeline, implement approval workflows that route changes to the right reviewers based on risk level, and leverage feature flags for controlled rollouts that satisfy speed and safety requirements.
5. What automation safeguards reduce release-related risks?
Examples of automation safeguards include:
- Automated security and compliance scanning that blocks problematic deployments
- Comprehensive test suites that catch regressions before production
- Progressive deployment capabilities that limit blast radius through canary releases
- Automated rollback triggers that revert changes when key metrics degrade,
- Real-time monitoring to roll back or deploy features as your tests reach certain thresholds

.webp)























































.png)
.png)

.png)

.png)



.png)



















.png)